An Internet-wide (IPv4) scan of externally accessible MQTT services
Introduction
As part of the VARIOT project, The Shadowserver Foundation has implemented an Internet-wide (IPv4) scan of externally accessible MQTT services. This scan was first announced on The Shadowserver Foundation’s website under the title “Open MQTT Report – Expanding the Hunt for Vulnerable IoT Devices“.
MQTT is a lightweight publish/subscribe protocol designed for the Internet of Things. As a generally poorly understood protocol, specifically designed for IoT, initial research conducted by The Shadowserver Foundation suggested it as a good candidate for evaluation as a possible first candidate for improving our IPv4 IoT scanning capability. Test scans were conducted, subsequently refined, until a full IPv4 scan was completed. Because we found the results to have a potentially high impact on Internet security of IoT devices (nearly 60% of the MQTT brokers discovered running on IoT devices allow for anonymous access as discovered in the initial scans), we quickly proceeded to incorporate the scan into production so as to alert the incident response community of the problems found.
How is the MQTT scan carried out?
The new MQTT scan involves attempting to connect to all 4 billion routable IPv4 addresses and querying for publicly accessible MQTT broker services enabled on port 1883/TCP. This is the default port for the MQTT broker, that operates as an unencrypted (plaintext) service. There is also a TLS enabled port 8883/TCP service, which is not yet included in the scan (due to the additional complexity of establishing TLS connections).
The goal of the MQTT scanning is to identify not just MQTT brokers exposed on the IPv4 internet, but in particular, MQTT instances that have no authentication enabled – allowing the broker to be anonymously accessed by anyone. This could mean that MQTT messages may be read, or potentially even published by a remote attacker. Additionally, as the MQTT service on port 1883/TCP is unencrypted, even user/password protected instances can still lead to data leakage if an attacker can observe the network traffic.
The MQTT scan is carried out using the standard 24 byte MQTT Connect command (for version MQTT 3.1.1) and captures the received response. MQTT version 5 devices should also respond to this command. The full IPv4 scan for port 1883/TCP itself returns over 3.2 million responses. Nearly all responses are from non-MQTT services. The full production scan takes around 30 minutes.
What do the scan results look like?
The first full test scan was carried out on the 11th March 2020, and the scan was implemented in production on 12th March 2020. After decoding the relevant MQTT responses, 71 508 devices were identified. Details on the statistics gathered from the first production scan can be found in the original Shadowserver blog post.
The daily scan for the 3rd May 2020 resulted in the discovery of 87 650 exposed devices around the world, over 16 000 more than from the first production scan. Nearly all of these can be attributed to South Korea.
The IP-geolocated country breakdown of the above reachable MQTT responses looks as follows:
Out of these exposed devices, 58 312 IPs allow for anonymous access. This is 66.5% of the accessible broker instances. The IP-geolocated country breakdown of the IP addresses that do allow anonymous access is as follows:
Nearly all the new MQTT devices that have appeared from South Korea have anonymous access enabled.
In the EU (+UK) the geo-location of the reachable MQTT devices is as follows:
A total of 18 238 devices are accessible. Out of these 8 711 are anonymously accessible (47.8%).
What do the EU statistics look like over time?
To provide some additional insight on the EU device distribution perspective, we have included an overview of how the MQTT numbers change over time for the EU MS in MQTT production scans.
As we can see currently, the numbers of reachable devices are more or less steady.
The country color codes from the tables below are reflected in the time series chart above, with the most accessible devices being in Germany, France and the Netherlands. The peak for anonymously accessible MQTT brokers was on the 30th of March 2020, while for reachable devices – 30th April 2020.
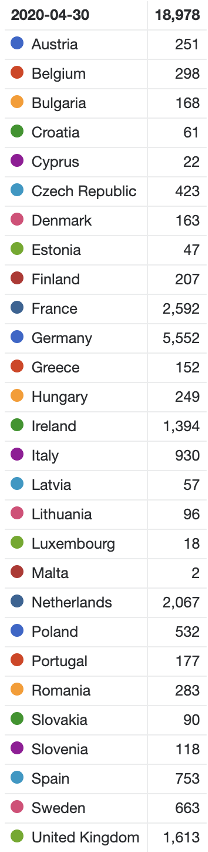
EU countries with reachable IPv4 MQTT – 30th April 2020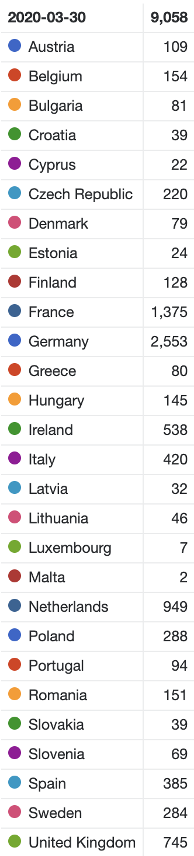
EU countries with reachable anonymously accessible IPv4 MQTT – 30th March 2020
A daily update of the production statistics from the MQTT scan can be found at the Shadowserver MQTT scan page.
Open MQTT report
All MQTT brokers that we find, along with the captured responses, are incorporated in a new free daily network report – the Open MQTT Report. Since March 13th 2020, the new MQTT report has been sent out daily, as part of our free victim remediation feeds to 109+ National CSIRTs and 4900+ network owners worldwide.
| Field | Description |
| timestamp | Time that the IP was probed in UTC+0 |
| ip | IP of the device in question |
| protocol | Transport layer protocol used (TCP) |
| port | Port being queried (usually 1883) |
| hostname | Reverse DNS name of the device in question |
| tag | Set to “mqtt” |
| asn | ASN announcing the scanning IP |
| geo | Country where the scanning IP resides |
| region | State / Province / Administrative region where the scanning IP resides |
| city | ASN of where the scanning IP resides |
| naics | North American Industry Classification System Code of the scanning IP |
| anonymous_access | Set to “Y” or “N” depending whether anonymous access is allowed |
| raw_response | Raw response to MQTT device probe |
| hex_code | The last octet of the raw response which tells you the connection status (00 – 05) |
| code | The human readable version of the hex_code |
A sample of what is being sent out on a daily basis looks like as follows:
"timestamp","ip","protocol","port","hostname","tag","asn","geo","region","city","naics","sic","anonymous_access","raw_response","hex_code","code"
"2020-03-12 17:03:45","122.35.229.163","tcp",1883,,"mqtt",17858,"KR","SEOUL TEUGBYEOLSI","SANGBONG-DONG",517311,0,"Y",20020000,00,"Connection Accepted"
"2020-03-12 17:03:45","47.93.162.196","tcp",1883,,"mqtt",37963,"CN",,"HANGZHOU",518210,0,"N",20020004,04,"Connection Refused, bad user name or password"
"2020-03-12 17:03:45","47.107.105.238","tcp",1883,,"mqtt",37963,"CN",,"HANGZHOU",518210,0,"N",20020005,05,"Connection Refused, not authorized"
"2020-03-12 17:03:45","139.224.13.57","tcp",1883,,"mqtt",37963,"CN",,"HANGZHOU",518210,0,"Y",20020000,00,"Connection Accepted"
"2020-03-12 17:03:45","116.9.122.71","tcp",1883,,"mqtt",4134,"CN",,"WUZHOU",517311,0,"Y",20020000,00,"Connection Accepted"
"2020-03-12 17:03:45","164.115.27.73","tcp",1883,,"mqtt",9835,"TH","KRUNG THEP MAHA NAKHON BANGKOK","SAI MAI",0,0,"N",20020005,05,"Connection Refused, not authorized"
Conclusion
We hope that the data being shared with Shadowserver’s free daily network report recipients will lead to a reduction of anonymously accessible MQTT broker services, as well as raise awareness among network owners and national CSIRTs to the potential exposure of data through non-encrypted services. Tips that the defender community can use to minimize the open MQTT broker footprint include:
- not needing to have your IoT device’s MQTT broker accessible from the Internet to everyone,
- enabling authentication of clients,
- firewalling to restricted clients only,
- enabling the broker on the SSL/TLS aware service on port 8883/TCP instead, to ensure that plaintext client/server authentication and communications are encrypted.
We believe that this new MQTT scan and report, as well as subsequent new IoT scans, will successfully demonstrate the direct positive impact of the VARIoT project on Internet security.
If you are not a subscriber to Shadowserver’s public benefit daily network reports but would like to receive this new report and our other existing 76 report types, then please sign up to our free daily remediation feed service. You can also check the updated statistics for this scan on our dedicated MQTT scan page.